This article describes the installation and configuration steps for Fortinet FortiGate 40F device. Similar instructions apply for 60F models. You need FortiOS v5.6 or above in order to proceed.
Log in to your FortiGate web interface.
The default URL to access the web UI through the network interface on port1 is:
https://192.168.1.99/
Go to User & Device > RADIUS Servers on the left menu.
Click Create New and configure:
Click OK to Save.
In the menu click User Groups and Create New.
Under Remote groups click Create New and under Remote Server choose Radius. Click OK to Save.
On the Policy & Objects > IP click Create New > Address.
Click OK to Save.
Next, click Create New > Address again and configure:
For each domain below you need to do as per above.
Under Addresses click Create New > Address Group and configure:
Click OK to Save.
Go to WiFi & Switch Controller > SSID on the left menu.
Click Create New > SSID and configure:
Click OK to Save.
Under IPv4 Policy click Create New and configure:
Click OK to Save.
Click Create New again and configure:
Click OK to Save changes.
Configure SSL VPN access for RADIUS users.
Example:
https://docs.fortinet.com
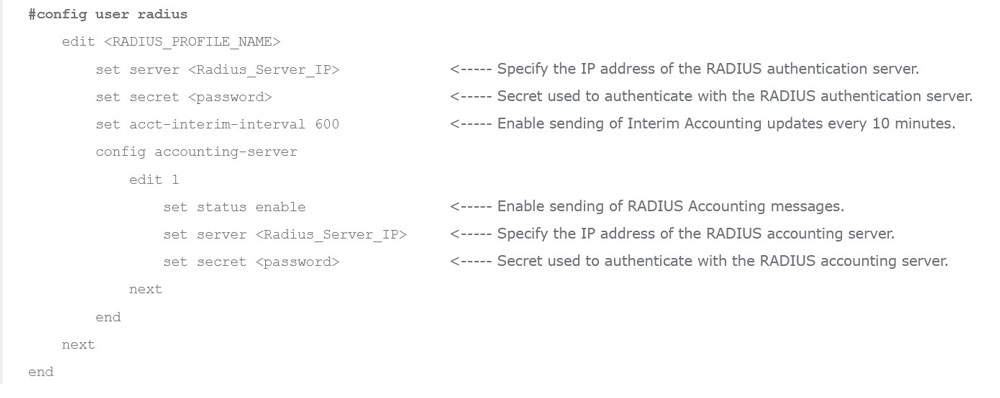
Configure FortiGate to send RADIUS Accounting:
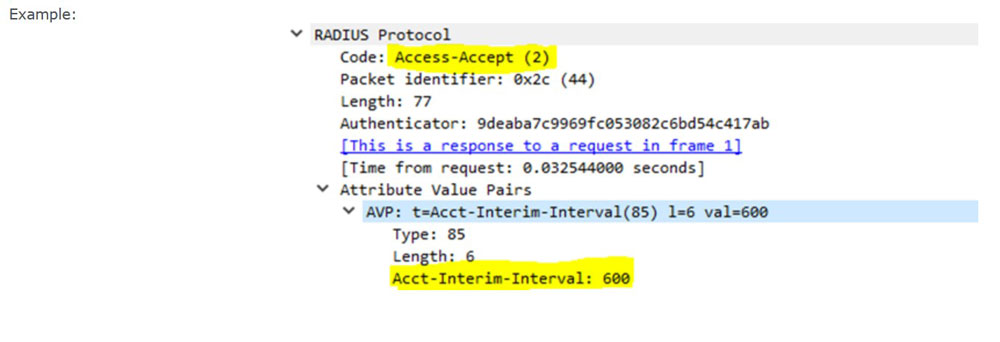
 Ensure the RADIUS server is configured to send AVP ‘Acct-Interim-Interval:600’ in the Access-Accept message.
Ensure the RADIUS server is configured to send AVP ‘Acct-Interim-Interval:600’ in the Access-Accept message.
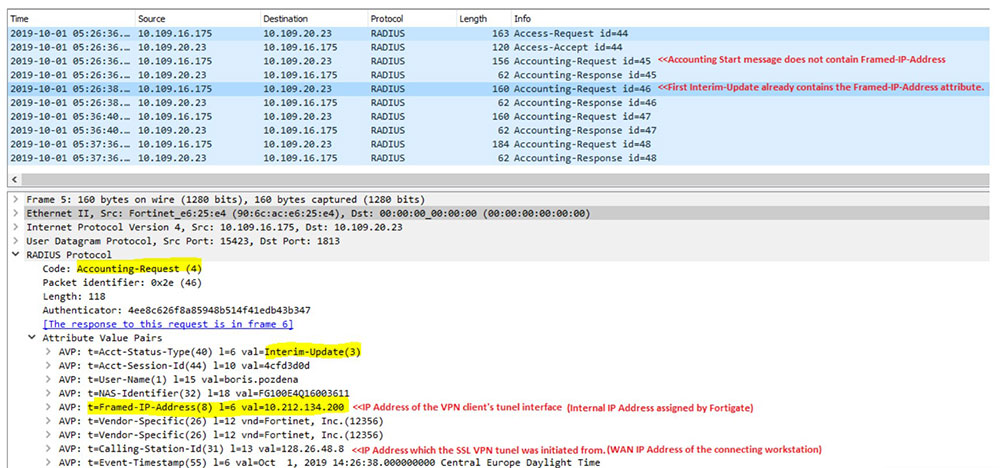
Verification of Configuration:
The bellow packet captures show the effect of the above configuration in action.

 Fortinet FortiGate
Fortinet FortiGate